1 Server side configuration
Activate the Keycloak feature and add configuration for user creation callbacks and initial groups:
feature:
keycloak: true
keycloak:
user_created_callback: your.companyname.custom.SsoUserCreated
init_groups: |
if(attr.roles.realm CONTAINSONEOF 'admin-user-role',
[3],
if(attr.roles.resource.gcms CONTAINSONEOF 'editor-user-role',
[4],
[5]
)
)
Place the `keycloak.json` generated for the CMS in the UI configuration directory (default: `ui-conf`).
2 Configuration for the Editor/Administration User Interface
If you are using the new UI, you will also have to make sure the REST-API is configured to use the Keycloak servlet filter.
Except for the groupMapper and userCreatedCallback entries, the configuration entries correspond exactly to the respective fields in the keycloak.json you can generate in the Keycloak admin front-end, and you should put all the entries here even when they are not listed in the example above.
2.1 Setup Content Security Policy
The Administrator User Interface requires some additional settings in Keycloak, to work as expected. Update the “Content Security Policy” of your Keycloak realm:
- Select your Realm in the top left corner
- Select the tab “Realm Settings” in the “Configure” category on the left sidebar
- Select the tab “Security Defenses” on the top bar
Adopt the “Content-Security-Policy” to allow the embedding from your CMS installation host:
frame-src 'self'; frame-ancestors 'self'; object-src 'none'; frame-src 'self'; frame-ancestors 'self' https://yourcmshost.tld; object-src 'none';
2.2 Using an Identity Provider
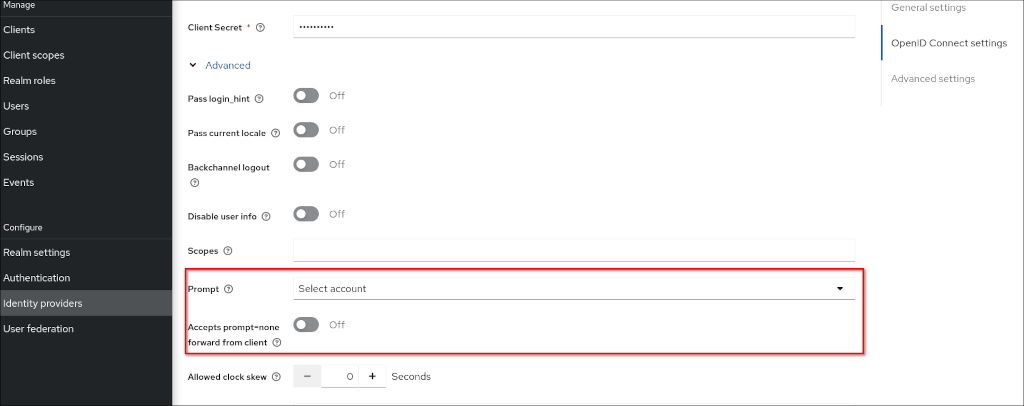
When using an identity provider the following two settings in the advanced OpenID Connect settings are important to prevent unwanted redirect behavior:
- “Prompt”: Set to “Select account”
- “Accepts prompt=none forward from client”: Set to “Off”
2.3 Circumvent Single Sign-on
It can usefull to not use the single sign process although it is enabled. The single sign on process will be skipped and users will be forwarded to the login form when the url parameter skip-sso is present. Example: https://yourcmshost.tld/editor/?skip-sso
2.4 Single Sign Out
By activating the feature
feature: keycloak_signout: true
users will automatically be logged out from Keycloak, if they log out from the CMS using the Editor User Interface or Administration User Interface.